Protecting legacy systems: risk assessment and security measures
What would happen if the backbone of your IT system failed? What if an outdated system turns into a security vulnerability in the middle of operations? The consequences of a core system going down are often severe: production interruptions, dissatisfied customers and contractual penalties.
Many organisations rely on IT systems that no longer reflect the current state of the art to run millions of business-critical processes every day. According to the study ‘Legacy Modernisation 2024‘, 72% of German companies are facing the challenge of modernising their outdated core business systems.
While these so-called legacy systems are functional and business-relevant, they entail considerable risks, including missing security updates, opaque dependencies, and outdated architectures, which make them a preferred target for cyberattacks.
However, a structured approach can ensure that even outdated systems are operated securely and reliably without the need for complete replacement. This article explains how modern risk assessment, threat modelling and middleware can be used to sustainably safeguard your legacy IT.
7 steps for identifying security gaps in legacy systems
Securing legacy systems requires a methodical approach, which involves identifying, assessing and prioritising risks rather than just reacting selectively.
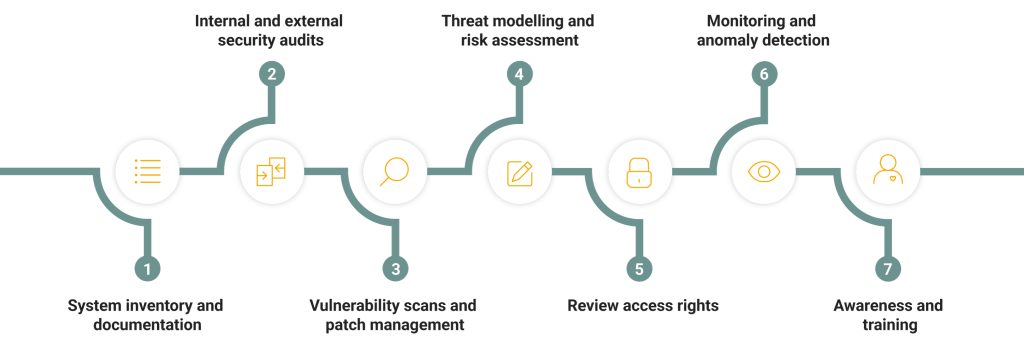
1. System inventory and documentation
Determine which legacy systems are still active, including the software, interfaces and hardware used. If up-to-date documentation is missing, it can be reconstructed through interviews with experienced employees and technical reverse analyses.
2. Internal and external security audits
Regular internal audits help verify compliance with your security policies. Complement these with external audits and penetration tests to avoid blind spots, particularly where outdated technologies make oversight more difficult.
3. Vulnerability scans and patch management
Legacy systems can be scanned for known vulnerabilities using specialised tools. If official updates are unavailable, bespoke solutions may be needed to implement compensating controls.
4. Threat modelling and risk assessment
What are realistic attack scenarios? What consequences would be faced by the company if a failure or data loss were to occur? And how likely is it to occur? Knowing the answers to these questions will help you take targeted action.
5. Review access rights
Over the years, permissions that are no longer required accumulate. Therefore, it is important to check them regularly and to rely on multi-factor authentication (MFA), role-based access control (RBAC) and the principle of least privilege. Just-in-time access and continuous authentication also increase security for particularly sensitive systems.
6. Monitoring and anomaly detection
Continuous monitoring helps to detect unusual patterns and potential attacks at an early stage. Use external anomaly detection tools that independently analyse and report suspicious activity.
7. Awareness and training
Technology only provides protection when used correctly. Provide role-specific training for operational technology personnel, administrators, and external service providers. In addition, conduct regular red team exercises tailored to legacy environments. A proven benchmark is two realistic scenarios per year.
Security starts with understanding
Good security decisions are based on analysis, not intuition. Especially with legacy systems, the following applies: what is unknown cannot be protected. Often, there is a lack of up-to-date overviews of data flows, interfaces, and dependencies, all of which form the foundation of any sound security strategy.
Holistic analysis: technology, context and impact
The criticality of a vulnerability depends on its context.
A test system with open ports is less critical than an ERP backend processing sensitive customer data. Technical findings should therefore always be assessed in light of the following questions:
- Which business processes rely on this system?
- What data does it process?
- How exposed is the system externally?
- What response time would be required in the event of an incident?
4 perspectives for a holistic view
Practical experience shows that an effective analysis model should combine the following four perspectives:
- Technology
Where are the specific vulnerabilities in code, architecture or configuration? - Business Impact
What would be the consequences of an attack or outage? - Attacker Logic
How attractive is this target to cybercriminals? - Probability of occurrence
How realistic is an attack scenario?
Only the combination of these four viewpoints results in a robust risk analysis that can withstand scrutiny from executive management or supervisory authorities.
Middleware and risk assessment for secure lagecy IT
Many legacy systems do not support modern authentication methods, encryption or logging. This is precisely the area in which middleware demonstrates its strength.
As an independent protective layer, it sits between the system and its environment. Security controls can be implemented through it without the need to modify the system itself.
This decoupling transforms middleware into a protective layer for systems that cannot be adapted, making it a vital component in achieving sustainable security in evolving IT landscapes.
Middleware as a security instance
Modern middleware can do much more than just transmit data. It acts as a strategic security centre and intelligently controls protective measures.
- Access control at user and role level (RBAC, MFA)
- Encryption of data streams and interface communication
- Logging, anomaly detection and real-time monitoring
- Blocking of suspicious requests
- Integration of modern security protocols (OAuth, SAML, TLS)
- Automatic response to incidents if required
In this way, the middleware becomes an active defender rather than just a ‘translator’ between systems.
Risk assessment for targeted protection
The central question is not whether middleware provides protection, but where and to what extent. A well-founded risk assessment forms the basis for securing the right systems at the appropriate depth and allocating resources effectively.
Example: An old booking system processes sensitive customer data and is connected to a modern web application via an API, but it cannot verify authentication itself. This responsibility is assumed by middleware. It requests credentials, validates them, and only forwards the request if authentication is successful. At the same time, it can detect attacks on the interface and block them automatically, leaving the legacy system to continue operating unchanged.
Sustainable security strategies for legacy systems
Legacy systems are not inherently insecure; they simply require a different security approach. With structured risk assessment, targeted threat modelling and integrated middleware solutions, outdated systems can be effectively protected and operated in the long term.
Proactive action not only minimises risks, but also strengthens the resilience of the entire organisation.
Contact
Are you looking for an experienced and reliable IT partner?
We offer customised solutions to meet your needs – from consulting, development and integration to operation.