Network resilience to protect business-critical infrastructure
Cyberattacks, natural disasters, or technical failures can have devastating effects on a company’s critical infrastructure. Neglecting network resilience is negligent and puts not only financial stability at risk, but also corporate reputation, customer trust, and legal compliance. Are you willing to leave your company’s future to chance? A robust network infrastructure is no longer optional. Network resilience is a key factor in ensuring the smooth operation and security of critical business infrastructures.
What is network resilience?
Network resilience is defined as a network’s ability to effectively absorb disruptions, adapt quickly, and restore normal operations without delay. For companies that depend on reliable IT systems, this capability is existential. A lack of diligence in this area jeopardizes overall business stability.
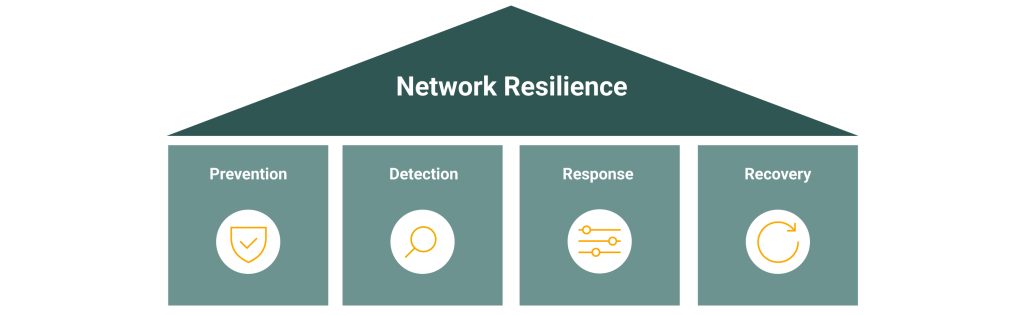
The 4 pillars of network resilience:
- Prevention:
Measures to minimise the likelihood and impact of potential disruptions through regular security updates, the use of firewalls and the implementation of access controls. - Detection:
Modern monitoring systems and analysis tools help to detect and analyse unusual activity at an early stage. - Response:
Rapid measures such as the immediate isolation of affected network segments and the initiation of countermeasures minimise the impact of disruption. - Recovery:
Well-designed recovery plans and regular backups ensure a swift return to normal operations after incidents are resolved.
Challenges for network resilience
Companies today face greater challenges than ever in securing the resilience of their networks:
- Cyberangriffe: DDoS-Attacken, Ransomware und Phishing können Netzwerke lahmlegen, den Geschäftsbetrieb massiv stören und zu erheblichen finanziellen Verlusten und einem Vertrauensverlust bei den Kunden führen.
- Naturkatastrophen: Brände, Erdbeben, Überschwemmungen oder Stürme können physische Schäden an der Netzwerkinfrastruktur verursachen und die Verfügbarkeit kritischer Dienste beeinträchtigen. Eine sorgfältige Planung und der Einsatz redundanter Systeme helfen, die Betriebsfähigkeit aufrechtzuerhalten.
- Technische Ausfälle: Hardwaredefekte, Softwarefehler oder menschliches Versagen können unvorhergesehene Netzwerkunterbrechungen verursachen, die ohne geeignete Backup- und Wiederherstellungsstrategien die Produktivität beeinträchtigen und zu Datenverlusten führen.
- Komplexität der Netzwerke: Moderne Netzwerke bestehen aus verschiedenen Komponenten und Technologien, was die Verwaltung und die Anfälligkeit für Störungen erhöht. Nur durch sorgfältige Planung und regelmäßige Überprüfung der Netzwerkinfrastruktur kann diese Komplexität bewältigt werden.
- Regulatorische Anforderungen: Immer strengere Compliance-Anforderungen an die Sicherheit und Verfügbarkeit der IT-Sicherheit erfordern kontinuierliche Anpassungen, Investitionen in Sicherheitstechnologien und umfassende Sicherheitsstrategien.
Strategies to strengthen network resilience
Strengthening network resilience requires a holistic approach. Organizations must combine proactive and comprehensive strategies to build robust and sustainable network infrastructures. The following section presents best practices that have proven themselves in practice.
1. Network design and architecture
- Redundancy: Implement redundant network paths and components to eliminate single points of failure. Backup connections and systems must be ready to take over immediately if a failure occurs.
- Segmentation: Divide the network into logical segments to limit the spread of disruptions and simplify management.
- Load balancing: Use load balancers to evenly distribute traffic across multiple servers, thereby increasing the network’s resilience.
2. Security measures
- Firewalls and intrusion detection systems (IDS): Deploy firewalls and IDS as the first line of defense to prevent unauthorized access and monitor suspicious activity.
- Encryption: Encrypt sensitive data during transmission and storage to prevent unauthorized access to critical information.
- Patch management: Make sure you regularly update and patch your systems and software to plug any security gaps and reduce the attack surface.
3. Monitoring and detection
- Network monitoring: Implement tools that monitor traffic and detect anomalies indicating potential disruptions.
- Logging: Capture and analyse network logs to identify suspicious activity and determine the causes of disruptions. Thorough analysis helps prevent future disruptions.
- Automated alerts: Set up automated alert systems to send immediate notifications to the IT team when disruptions are detected. This enables the team to intervene promptly and resolve issues.
4. Emergency planning and recovery
- Disaster Recovery Plan (DRP): Develop a comprehensive DRP that is regularly tested and updated, covering all possible scenarios and recovery measures.
- Backup strategies: Perform regular, automated backups of critical data and systems and store them securely in accessible locations.
- Emergency drills: Conduct regular emergency drills to test the effectiveness of your DRP, reduce response times and increase resilience, while also preparing the IT team for real-life incidents.
5. Training and awareness
- Employee training: Provide regular training on network security, detection mechanisms and response strategies. Well-trained personnel can recognise and mitigate threats at an early stage.
- Awareness campaigns: Run awareness initiatives to strengthen understanding of potential threats and best practices. A well-informed workforce is crucial in preventing security incidents.
Practical example: network resilience in practice with 7P
7P supported a leading service provider in implementing a comprehensive, group-wide network resilience policy. The objective was to continuously monitor critical infrastructure and ensure compliance with all resilience requirements. 7P enhanced the overall resilience strategy through targeted measures. Even during crisis scenarios, critical services remain reliably available, thereby strengthening customer trust and safeguarding long-term brand integrity.
The policy covers several scenarios that could have a significant impact on mobile and/or fixed-line customers, revenue and the company’s image:
- Full site loss: Implementing redundancies and backup systems enables data traffic to be automatically redirected to one or more secondary sites in the event of total infrastructure failure, thereby ensuring service continuity and minimising downtime.
- Full virtualized application loss: A comprehensive backup/restore solution (Cybervault) can prevent a complete failure of the virtualised network environment due to cyber-attacks, such as ransomware. It allows the virtual infrastructure and all critical network functions hosted on it to be recovered rapidly.
- GPS failure: If the GPS fails, the system automatically switches to an alternative time source. This maintains network coverage and functionality, ensuring uninterrupted operations.
Ensuring successfull implementation through 7P
| Appointment and announcement of relevant roles | All roles relevant to the implementation of the policy controls were filled and announced in the market. |
| Establishment of efficient processes | To ensure smooth operation, efficient processes were established to comply with network resilience guidelines. |
| Updating of site risk assessments | All site risk assessments have been continuously updated and a coordinated and approved action plan has been developed. |
| Maintenance of critical infrastructure | The list of critical infrastructure and the assessment of service-level targets were updated regularly. |
| Risk assessments for new sites | Comprehensive risk assessments for new sites, services and major changes were carried out and their impact communicated. |
| Updating critical documents | All important documentation is always up to date, available and properly archived. |
| Disaster recovery plans | Comprehensive disaster recovery plans for critical infrastructure were created and updated regularly. |
| Regular testing of recovery plans | All disaster recovery plans are regularly tested to ensure they are effective. |
| Review of contracts | Conduct regular reviews of contracts with third-party providers and outsourcers, adapting them to align with the Network Resilience Guidelines. |
| Reporting on policy violations | In cases of policy violations or near misses, detailed reports were prepared, including a root-cause analysis and details of the corrective actions taken. |
| Implementation of lessons learned and corrective actions | Lessons learned and corrective actions from all policy controls, security reviews and audits were implemented within agreed timelines. |
| Consolidated report | Every three months, a consolidated report on the status of all policy controls was created for senior management. |
| SteerCo meetings | Regular SteerCo meetings were prepared and moderated to keep all stakeholders informed. |
| Dry runs for quality improvement | Dry runs to review and improve the quality of policy controls (processes, evidence) were prepared and conducted. |
| Awareness measures and training | Awareness measures and training on network resilience are needed to strengthen employee awareness and capability. |
The strategic governance provided by 7P was a significant factor in the successful implementation of network resilience measures. Its structured approach and clear communication enabled internal teams to comply fully with all policy requirements.
Network resilience – key takeaways
A network’s ability to absorb disruptions, adapt and recover quickly is essential to maintaining business-critical processes and services. Therefore, the use of network resilience is a fundamental element in protecting a company’s critical infrastructure. Companies face challenges such as cyber-attacks, natural disasters, technical failures, the complexity of modern networks and strict regulatory demands. Addressing these challenges requires a holistic strategy to strengthen network robustness.
Contact
Are you looking for an experienced and reliable IT partner?
We offer customised solutions to meet your needs – from consulting, development and integration to operation.